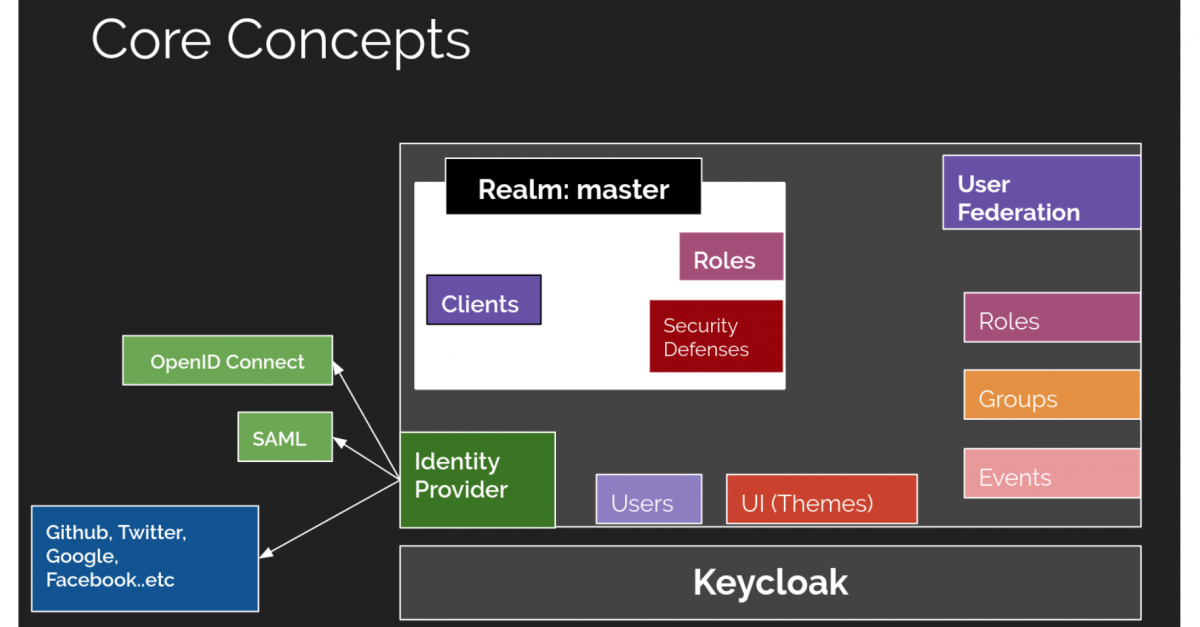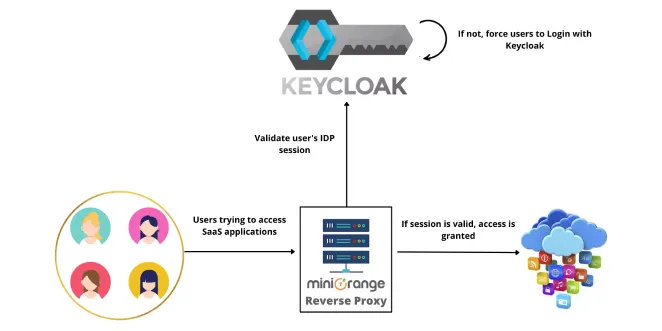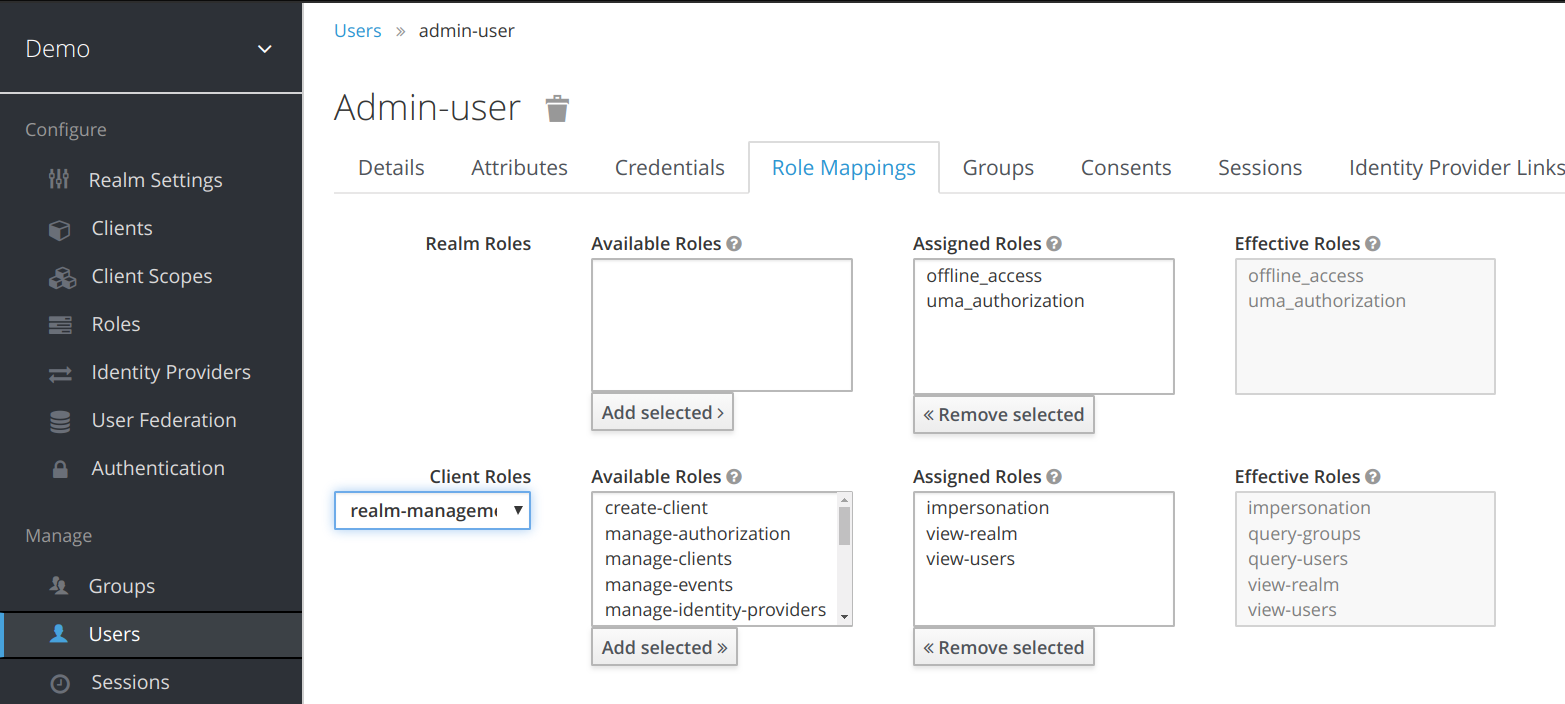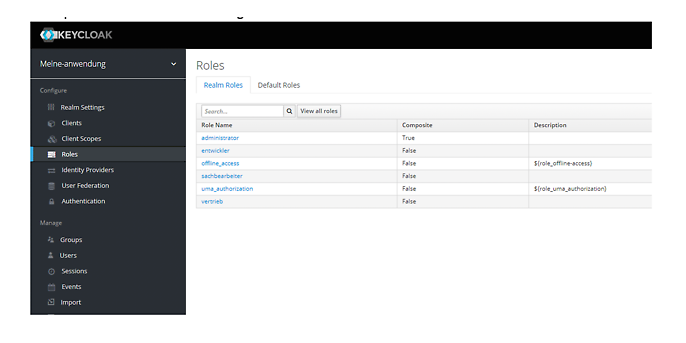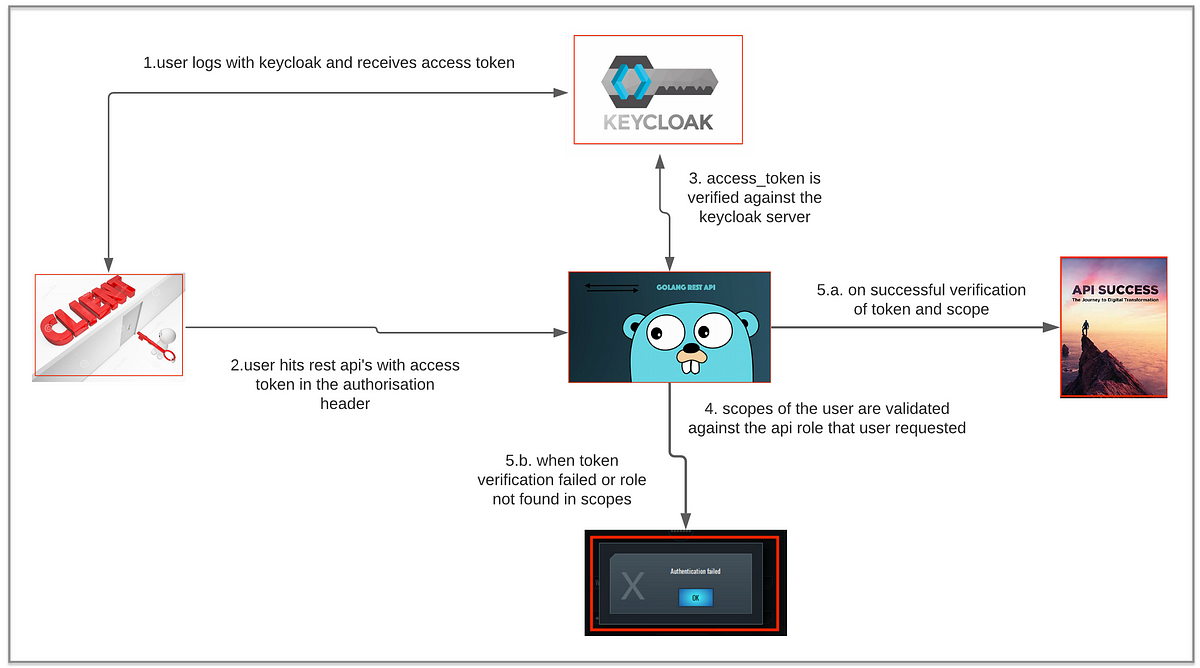
Authentication and Authorization (OpenID Connect)of Go Rest Api's using an open-source IAM called Keycloak | by Allu Sai Prudhvi | Medium
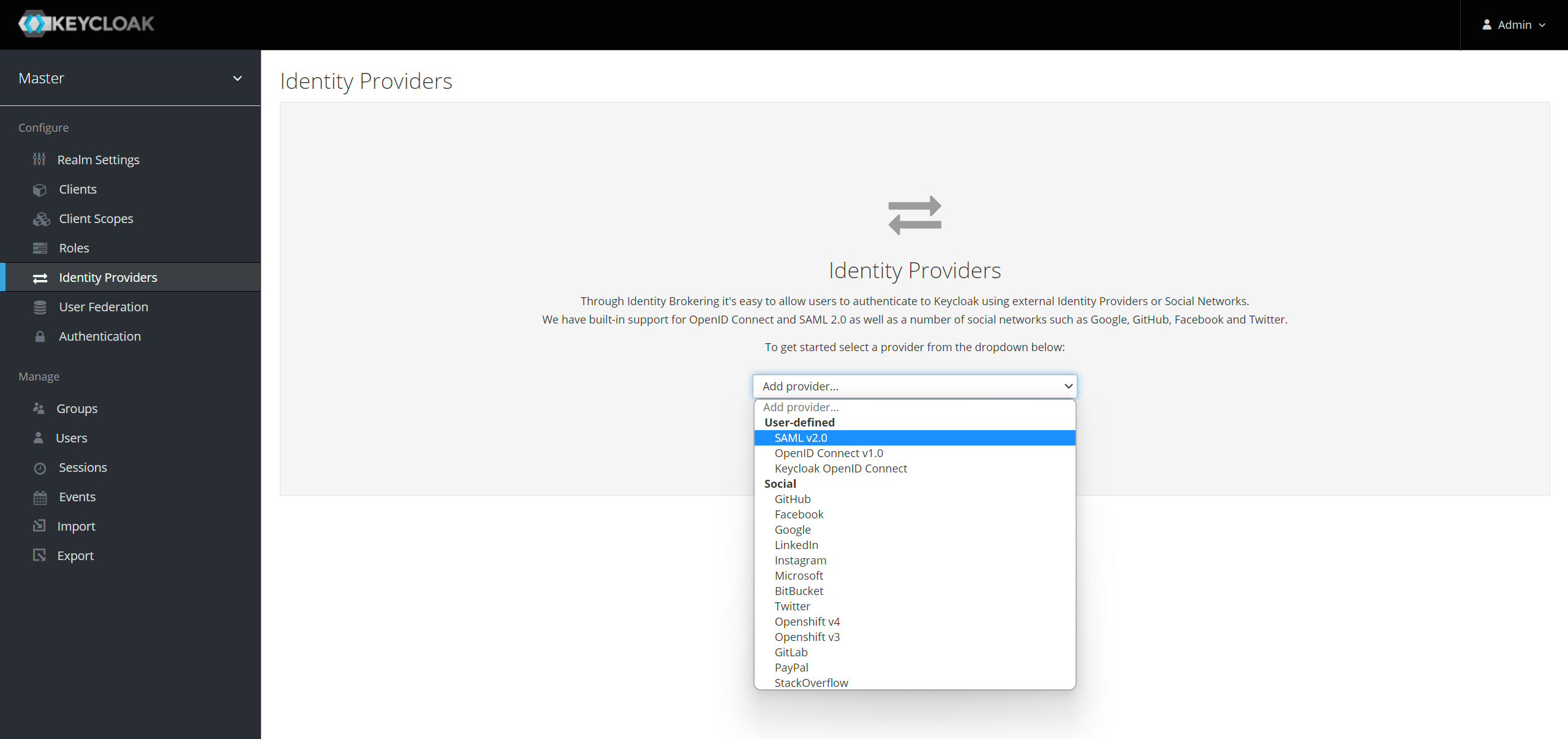
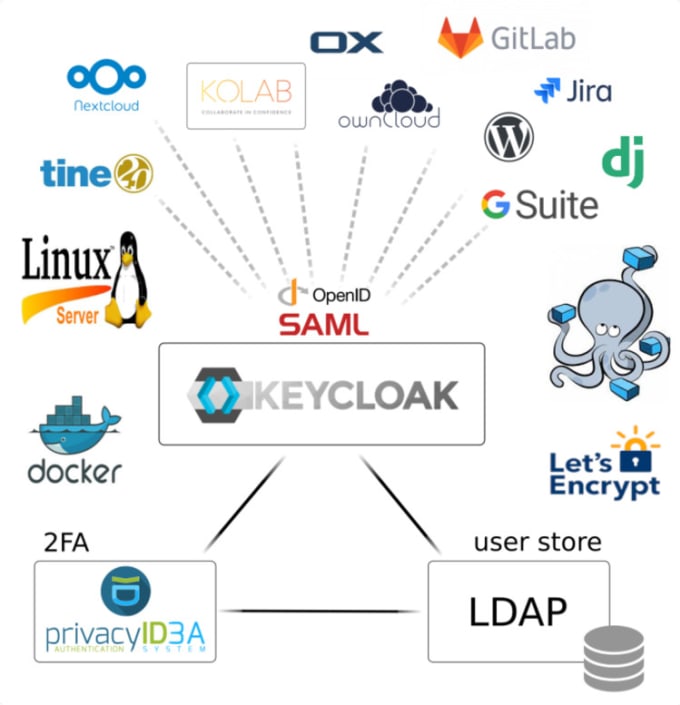
Keycloak | Casdoor · An Open Source UI-first Identity Access Management (IAM) / Single-Sign-On (SSO) platform supporting OAuth 2.0, OIDC, SAML and CAS
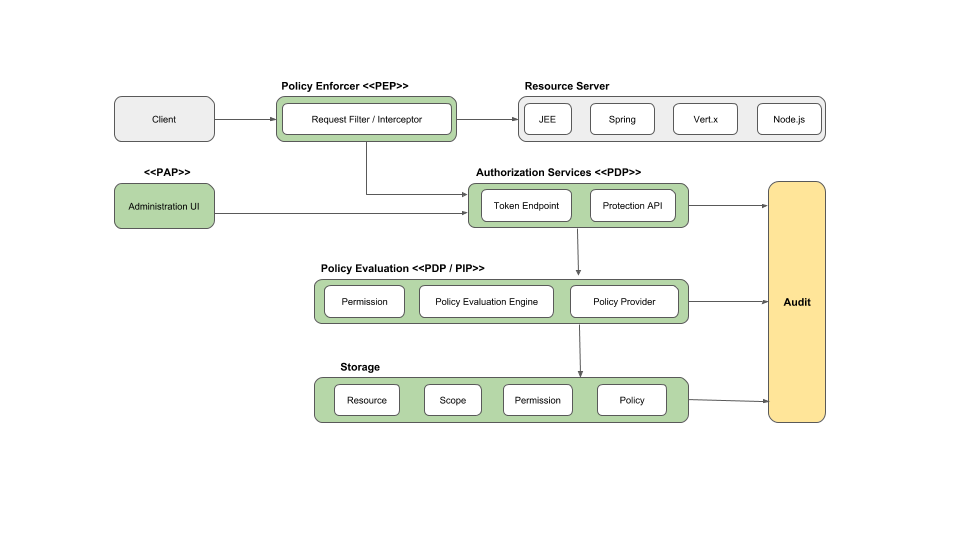
Introduction to Building an Effective Identity and Access Management Architecture with Keycloak | by Santosh Shinde | Medium